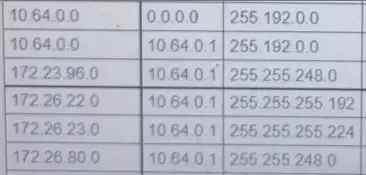
Yo creo que esta relaciono con que han pasado a firewall4.
Paquetes instalados:
base-files bird1-IPv4 bird1-IPv4-uci bnx2-firmware busybox ca-bundle cgi-io collectd collectd-mod-cpu collectd-mod-interface collectd-mod-iwinfo collectd-mod-load collectd-mod-memory collectd-mod-network collectd-mod-rrdtool collectd-mod-thermal ddns-scripts ddns-scripts-services dnsmasq dropbear e2fsprogs eoip firewall fstools fwtool getrandom gre grub2 grub2-efi hostapd hostapd-common ip6tables-nft iptables-nft jansson4 jshn jsonfilter kernel kmod-Amazon-ena kmod-amd-xgbe kmod-bnx2 kmod-button-hotplug kmod-crypto-crc32c kmod-crypto-hash kmod-crypto-kpp kmod-crypto-lib-chacha20 kmod-crypto-lib-chacha20poly1305 kmod-crypto-lib-curve25519 kmod-crypto-lib-poly1305 kmod-e1000 kmod-e1000e kmod-forcedeth kmod-fs-vfat kmod-gre kmod-gre6 kmod-hwmon-core kmod-i2c-algo-bit kmod-i2c-core kmod-igb kmod-igc kmod-input-core kmod-ip6-tunnel kmod-ip6tables kmod-ipt-conntrack kmod-ipt-conntrack-extra kmod-ipt-core kmod-ipt-NAT kmod-ipt-nathelper-rtsp kmod-ipt-offload kmod-iptunnel kmod-iptunnel6 kmod-ixgbe kmod-lib-crc-ccitt kmod-lib-crc32c kmod-libphy kmod-mdio kmod-mdio-devres kmod-mii kmod-nf-conntrack kmod-nf-conntrack6 kmod-nf-flow kmod-nf-ipt kmod-nf-ipt6 kmod-nf-log kmod-nf-log6 kmod-nf-NAT kmod-nf-reject kmod-nf-reject6 kmod-nfnetlink kmod-nft-compat kmod-nft-core kmod-nft-NAT kmod-nft-offload kmod-nls-base kmod-nls-cp437 kmod-nls-iso8859-1 kmod-nls-utf8 kmod-phy-realtek kmod-ppp kmod-PPPoE kmod-pppox kmod-pps kmod-ptp kmod-r8169 kmod-slhc kmod-tg3 kmod-tun kmod-udptunnel4 kmod-udptunnel6 kmod-wireguard libblkid1 libblobmsg-json20220515 libc libcomerr0 libevdev libext2fs2 libf2fs6 libgcc1 libip4tc2 libip6tc2 libiptext-nft0 libiptext0 libiptext6-0 libiwinfo-data libiwinfo-lua libiwinfo20210430 libjson-c5 libjson-script20220515 libltdl7 liblua5.1.5 liblucihttp-lua liblucihttp0 liblzo2 libmnl0 libncurses6 libnftnl11 libnl-tiny1 libpthread librrd1 librt libsmartcols1 libss2 libubox20220515 libubus-lua libubus20220601 libuci-lua libuci20130104 libuclient20201210 libudev-zero libusb-1.0-0 libustream-wolfssl20201210 libuuid1 libwolfssl5.4.0.ee39414e libxtables12 logd lua luci luci-app-bird1-IPv4 luci-app-ddns luci-app-eoip luci-app-firewall luci-app-opkg luci-app-statistics luci-app-watchcat luci-app-wireguard luci-base luci-lib-base luci-lib-IP luci-lib-ipkg luci-lib-jsonc luci-lib-nixio luci-mod-admin-full luci-mod-network luci-mod-status luci-mod-system luci-proto-IPv6 luci-proto-ppp luci-proto-wireguard luci-ssl luci-theme-bootstrap mkf2fs mtd nano netifd nftables-json odhcp6c odhcpd-ipv6only omcproxy OpenWrt-keyring opkg partx-utils ppp ppp-mod-PPPoE procd procd-seccomp procd-ujail px5g-wolfssl r8169-firmware resolveip rpcd rpcd-mod-file rpcd-mod-iwinfo rpcd-mod-luci rpcd-mod-rrdns rrdtool1 terminfo ubox ubus ubusd uci uclient-fetch uhttpd uhttpd-mod-ubus urandom-seed urngd usbids usbutils usign watchcat wireguard-tools xtables-nft zlib
Bird4.conf:
log syslog all;
protocol kernel {
persist;
scan time 20;
import all;
export all;
}
protocol device {
scan time 10;
}
filter voip_filter {
if net ~ 10.0.0.0/8 then accept;
else reject;
}
protocol rip VoIP {
import all;
export filter voip_filter;
interface "eth5.3";
}
filter iptv_filter {
if net ~ 172.16.0.0/12 then accept;
else reject;
}
protocol rip iptv {
import all;
export filter iptv_filter;
interface "eth5.2";
}
Sysctl:
net.netfilter.nf_conntrack_helper=1
Network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config device
option name 'br-LAN'
option type 'bridge'
option igmp_snooping '1'
list ports 'eth0'
list ports 'eth1'
list ports 'eth2'
list ports 'eth3'
list ports 'eth4'
config interface 'LAN'
option device 'br-LAN'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.3.1'
option IPv6 '0'
option delegate '0'
list DNS '1.1.1.1'
list DNS '8.8.8.8'
config device
option type 'bridge'
option name 'bridge-iptv'
option bridge_empty '1'
option igmp_snooping '1'
config interface 'WAN'
option proto 'PPPoE'
option username 'adslppp@telefonicanetpa'
option password 'adslppp'
option device 'eth5.6'
option IPv6 '0'
option peerdns '0'
list DNS '1.1.1.1'
list DNS '8.8.8.8'
config interface 'IPTV'
option proto 'static'
option ipaddr '10.195.118.235'
option gateway '10.128.0.1'
option device 'eth5.2'
option netmask '255.0.0.0'
config device
option type '8021q'
option ifname 'eth5'
option vid '6'
option name 'eth5.6'
config device
option type '8021q'
option ifname 'eth5'
option vid '3'
option name 'eth5.3'
config device
option type '8021q'
option ifname 'eth5'
option vid '2'
option name 'eth5.2'
config interface 'VoIP'
option proto 'DHCP'
option device 'eth5.3'
option auto '0'
Firewall:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'LAN'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'LAN'
config zone
option name 'WAN'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'WAN'
config forwarding
option src 'LAN'
option dest 'WAN'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'WAN'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'IPv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'WAN'
option dest 'LAN'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'WAN'
option dest 'LAN'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'VPN'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'VPN'
option masq '1'
config forwarding
option src 'LAN'
option dest 'VPN'
config forwarding
option src 'VPN'
option dest 'LAN'
config rule
list proto 'udp'
option src 'WAN'
option target 'ACCEPT'
option name 'Allow-WireguardServer'
option dest_port '51821'
config zone
option name 'vpn_server'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'vpn_server'
config forwarding
option src 'vpn_server'
option dest 'LAN'
config forwarding
option src 'LAN'
option dest 'vpn_server'
config rule
option name 'Allow-GRE-EOIP'
list proto 'gre'
option src 'vpn_server'
option dest '*'
option target 'ACCEPT'
config zone
option name 'VoIP'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
list network 'VoIP'
config zone
option name 'iptv'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'IPTV'
config forwarding
option src 'LAN'
option dest 'VoIP'
config forwarding
option src 'iptv'
option dest 'LAN'
config forwarding
option src 'LAN'
option dest 'iptv'
config redirect
option dest 'LAN'
option target 'DNAT'
list proto 'tcp'
option src 'WAN'
option src_dport '80'
option dest_ip '192.168.3.2'
option name 'http'
config redirect
option dest 'LAN'
option target 'DNAT'
list proto 'tcp'
option src 'WAN'
option src_dport '443'
option name 'https'
option dest_ip '192.168.3.2'