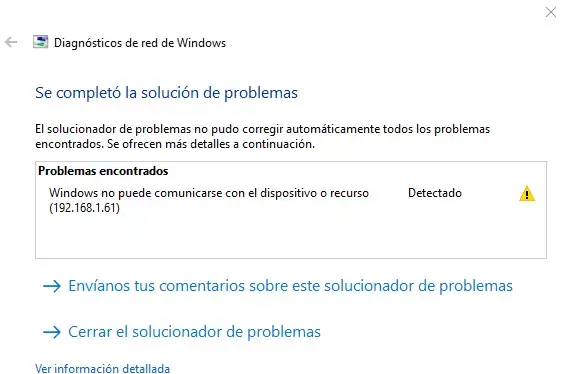
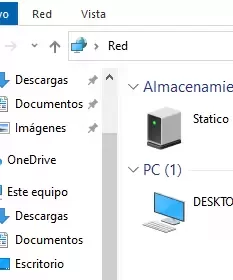
La configuración es la siguiente, ya he probado a deshabilitar todo el firewall/mangle/raw y sigo sin poder ver el NAS ni imprimir en red
# mar/27/2020 16:49:45 by RouterOS 6.46.3
# software id =
#
# model =
# serial number =
/interface bridge
add name=bridge1
/interface wireless
set [ find default-name=wlan2 ] antenna-gain=0 band=2ghz-b/g/n channel-width=\
20/40mhz-XX country=no_country_set default-authentication=no disabled=no \
frequency=auto mode=ap-bridge name=wlan1 ssid=nolink wds-ignore-ssid=yes
set [ find default-name=wlan1 ] antenna-gain=0 band=5ghz-a/n/ac \
channel-width=20/40/80/160mhz-XXXXXXXX country=no_country_set \
frequency-mode=superchannel hide-ssid=yes mac-address=:D6 \
mode=bridge multicast-helper=disabled name=wlan2 radio-name=D6 \
ssid=Hot_Spot wps-mode=disabled
/interface ethernet
set [ find default-name=ether1 ] mac-address=74:4D:28:
set [ find default-name=ether2 ] mac-address=74:4D:28:
set [ find default-name=ether3 ] mac-address=74:4D:28:
set [ find default-name=ether4 ] mac-address=74:4D:28:
set [ find default-name=ether5 ] mac-address=74:4D:28:
set [ find default-name=ether6 ] mac-address=74:4D:28:
set [ find default-name=ether7 ] mac-address=74:4D:28:
set [ find default-name=ether8 ] mac-address=74:4D:28:
set [ find default-name=ether9 ] mac-address=74:4D:28:
set [ find default-name=ether10 ] mac-address=74:4D:28:
set [ find default-name=sfp-sfpplus1 ] mac-address=74:4D:28:
/interface vlan
add interface=ether1 name=vlan6 vlan-id=6
/interface pppoe-client
add add-default-route=yes disabled=no interface=vlan6 name=internet user=\
adslppp@telefonicanetpa
/interface ethernet switch port
set 0 default-vlan-id=0
set 1 default-vlan-id=0
set 2 default-vlan-id=0
set 3 default-vlan-id=0
set 4 default-vlan-id=0
set 5 default-vlan-id=0
set 6 default-vlan-id=0
set 7 default-vlan-id=0
set 8 default-vlan-id=0
set 9 default-vlan-id=0
set 10 default-vlan-id=0
set 11 default-vlan-id=0
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
add authentication-types=wpa-psk,wpa2-psk eap-methods="" group-ciphers=\
tkip,aes-ccm mode=dynamic-keys name=xx supplicant-identity=\
xx unicast-ciphers=tkip,aes-ccm
/interface wireless
add disabled=no keepalive-frames=disabled mac-address=76:4D:28: \
master-interface=wlan1 multicast-buffering=disabled name=hp \
security-profile=xx ssid="HP" \
wds-cost-range=0 wds-default-cost=0 wps-mode=disabled
/ip pool
add name=dchp_pool2 ranges=192.168.1.2-192.168.1.5
add name=dhcp_pool1 ranges=192.168.10.2-192.168.10.5
/ip dhcp-server
add address-pool=dchp_pool2 disabled=no insert-queue-before=bottom interface=\
bridge1 name=dchp2
add address-pool=dhcp_pool1 disabled=no insert-queue-before=bottom interface=\
hp-print name=dhcp1
/system logging action
set 0 memory-lines=10000
set 1 disk-lines-per-file=10000
/caps-man manager
set enabled=yes
/interface bridge port
add bridge=bridge1 comment=defconf interface=ether2
add bridge=bridge1 comment=defconf interface=ether3
add bridge=bridge1 comment=defconf interface=ether4
add bridge=bridge1 comment=defconf interface=ether5
add bridge=bridge1 comment=defconf interface=ether6
add bridge=bridge1 comment=defconf interface=ether7
add bridge=bridge1 comment=defconf interface=ether8
add bridge=bridge1 comment=defconf interface=ether9
add interface=*D
add bridge=bridge1 interface=ether10
add interface=*14
add interface=ether1
add interface=sfp-sfpplus1
add interface=*C
add bridge=bridge1 disabled=yes interface=hp
/interface bridge settings
set use-ip-firewall=yes
/ip neighbor discovery-settings
set discover-interface-list=LAN
/ip settings
set tcp-syncookies=yes
/interface list member
add interface=ether2 list=LAN
add interface=ether3 list=LAN
add interface=ether4 list=LAN
add interface=ether5 list=LAN
add interface=ether6 list=LAN
add interface=ether7 list=LAN
add interface=ether8 list=LAN
add interface=ether9 list=LAN
add interface=ether10 list=LAN
add interface=sfp-sfpplus1 list=LAN
add list=LAN
add disabled=yes list=WAN
add interface=ether1 list=LAN
add interface=internet list=WAN
/interface ovpn-server server
set auth=sha1 cipher=aes256 enabled=yes require-client-certificate=yes
/interface wireless cap
set interfaces=*C,*D
/ip address
add address=192.168.10.1/24 interface=hp network=192.168.10.0
add address=192.168.1.1/24 interface=bridge1 network=192.168.1.0
/ip dhcp-server network
add address=192.168.1.0/24 dns-server=1.1.1.1 gateway=192.168.1.1 netmask=24
add address=192.168.10.0/24 dns-server=1.1.1.1 gateway=192.168.10.1
/ip dns
set allow-remote-requests=yes servers=1.1.1.1,1.0.0.1
/ip dns static
add address=192.168.11.1 name=router.lan
/ip firewall address-list
/ip firewall filter
add action=drop chain=virus dst-port=\
135-139,445,593,4000,4444,995-999,8998,2745,4751,1434 protocol=tcp
add action=drop chain=virus dst-port=\
135-139,445,593,4000,4444,995-999,8998,2745,4751,1434 protocol=udp
add action=jump chain=forward comment="Virus Flood Protect" connection-state=\
new jump-target=virus protocol=tcp tcp-flags=syn
add action=jump chain=forward comment="jump to the virus chain" jump-target=\
virus
add action=accept chain=virus connection-state=new limit=400,5:packet \
protocol=tcp tcp-flags=syn
add action=drop chain=virus connection-state=new protocol=tcp tcp-flags=syn
add action=drop chain=input dst-port=22 protocol=tcp
add action=drop chain=known_viruses comment=" windows not EXACTLY a virus" \
dst-port=135-139,445,593,4444,4000,995-999,8998,2745,4751,1434 protocol=\
tcp
add action=drop chain=known_viruses comment=" windows not EXACTLY a virus" \
dst-port=135-139,445,593,4444,4000,995-999,8998,2745,4751,1434 protocol=\
udp
add action=jump chain=forward comment="SYN Flood Protect" connection-state=\
new jump-target=SYN-Protect protocol=tcp tcp-flags=syn
add action=accept chain=SYN-Protect connection-state=new limit=400,5 \
protocol=tcp tcp-flags=syn
add action=drop chain=SYN-Protect connection-state=new protocol=tcp \
tcp-flags=syn
add action=add-src-to-address-list address-list=acceso-winbox chain=input \
dst-port=8291 protocol=tcp
add action=drop chain=forward comment="drop MAC" src-mac-address=\
38:4F:49:88:B9:BF
add action=drop chain=ICMP comment=" 0:0 and limit for 5pac/s" icmp-options=\
0:0-255 limit=5,5:packet protocol=icmp
add action=drop chain=ICMP comment="3:3 and limit for 5pac/s" icmp-options=\
3:3 limit=5,5:packet protocol=icmp
add action=drop chain=ICMP comment="3:4 and limit for 5pac/s" \
icmp-options=3:4 limit=5,5:packet protocol=icmp
add action=drop chain=ICMP comment="8:0 and limit for 5pac/s" icmp-options=\
8:0-255 limit=5,5:packet protocol=icmp
add action=drop chain=ICMP comment=" 11:0 and limit for 5pac/s" icmp-options=\
11:0-255 limit=5,5:packet protocol=icmp
add action=drop chain=ICMP comment="Drop everything else" protocol=icmp
add action=add-src-to-address-list address-list="Lista Negra" \
address-list-timeout=1d chain=input comment="Deteccion de DOS" \
connection-limit=100,32
add action=drop chain=forward comment="Block Atakante DOS" protocol=tcp \
src-address-list="Lista Negra"
add action=tarpit chain=input comment=\
"*************Impedir Atacante DOS genere nuevas conecxiones" protocol=\
tcp src-address-list="Lista Negra"
add action=drop chain=forward comment=\
"*************BLOCK SPAMMERS OR INFECTED USERS" dst-port=25 protocol=tcp \
src-address-list=spammer
add action=add-src-to-address-list address-list=spammer address-list-timeout=\
1d chain=forward comment="Detect and add-list SMTP virus or spammers" \
connection-limit=30,32 dst-port=25 limit=50,5 protocol=tcp
add action=accept chain=ICMP comment="0:0 and limit for 5pac/s" icmp-options=\
0:0-255 limit=5,5 protocol=icmp
add action=accept chain=ICMP comment="3:3 and limit for 5pac/s" icmp-options=\
3:3 limit=5,5 protocol=icmp
add action=accept chain=ICMP comment="3:4 and limit for 5pac/s" icmp-options=\
3:4 limit=5,5 protocol=icmp
add action=accept chain=ICMP comment="8:0 and limit for 5pac/s" icmp-options=\
8:0-255 limit=5,5 protocol=icmp
add action=accept chain=ICMP comment="11:0 and limit for 5pac/s" \
icmp-options=11:0-255 limit=5,5 protocol=icmp
add action=drop chain=ICMP comment="Drop everything else" protocol=icmp
add action=drop chain=forward comment="no ping" log=yes protocol=icmp
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=drop chain=input comment="defconf: accept ICMP" log=yes protocol=\
icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
add action=drop chain=input comment="drop ssh brute forcers" dst-port=22 \
protocol=tcp src-address-list=ssh_blacklist
add action=add-src-to-address-list address-list=ssh_blacklist \
address-list-timeout=1w3d chain=input connection-state=new dst-port=22 \
protocol=tcp src-address-list=ssh_stage3
add action=add-src-to-address-list address-list=ssh_stage3 \
address-list-timeout=1m chain=input connection-state=new dst-port=22 \
protocol=tcp src-address-list=ssh_stage2
add action=add-src-to-address-list address-list=ssh_stage2 \
address-list-timeout=1m chain=input connection-state=new dst-port=22 \
protocol=tcp src-address-list=ssh_stage1
add action=add-src-to-address-list address-list=ssh_stage1 \
address-list-timeout=1m chain=input connection-state=new dst-port=22 \
protocol=tcp
/ip firewall mangle
add action=mark-connection chain=prerouting comment=DNS connection-state=new \
new-connection-mark=DNS port=53 protocol=udp
add action=mark-packet chain=prerouting connection-mark=DNS new-packet-mark=\
DNS passthrough=no
add action=mark-connection chain=postrouting connection-state=new \
new-connection-mark=DNS port=53 protocol=udp
add action=mark-packet chain=postrouting connection-mark=DNS new-packet-mark=\
DNS passthrough=no
add action=mark-connection chain=prerouting comment=VOIP new-connection-mark=\
VOIP port=5060,5061,10000-20000 protocol=udp
add action=mark-packet chain=prerouting connection-mark=VOIP new-packet-mark=\
VOIP passthrough=no
add action=mark-connection chain=prerouting comment=UDP connection-state=new \
new-connection-mark=UDP protocol=udp
add action=mark-packet chain=prerouting connection-mark=UDP new-packet-mark=\
UDP passthrough=no
add action=mark-connection chain=prerouting comment=ICMP connection-state=new \
new-connection-mark=ICMP protocol=icmp
add action=mark-packet chain=prerouting connection-mark=ICMP new-packet-mark=\
ICMP passthrough=no
add action=mark-connection chain=postrouting connection-state=new \
new-connection-mark=ICMP protocol=icmp
add action=mark-packet chain=postrouting connection-mark=ICMP \
new-packet-mark=ICMP passthrough=no
add action=mark-packet chain=postrouting comment=ACK new-packet-mark=ACK \
packet-size=0-123 passthrough=no protocol=tcp tcp-flags=ack
add action=mark-packet chain=prerouting new-packet-mark=ACK packet-size=0-123 \
passthrough=no protocol=tcp tcp-flags=ack
add action=mark-connection chain=prerouting comment=HTTP connection-mark=\
!HTTP_BIG connection-state=new new-connection-mark=HTTP port=80,443 \
protocol=tcp
add action=mark-connection chain=prerouting connection-bytes=500000-0 \
connection-mark=HTTP connection-rate=200k-100M new-connection-mark=\
HTTP_BIG protocol=tcp
add action=mark-packet chain=prerouting connection-mark=HTTP_BIG \
new-packet-mark=HTTP_BIG passthrough=no
add action=mark-packet chain=prerouting connection-mark=HTTP new-packet-mark=\
HTTP passthrough=no
add action=mark-connection chain=prerouting comment=OTHER connection-mark=\
no-mark new-connection-mark=OTHER
add action=mark-packet chain=prerouting connection-mark=OTHER \
new-packet-mark=OTHER passthrough=no
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface=internet out-interface-list=WAN
/ip firewall raw
add action=drop chain=prerouting protocol=tcp src-port=\
135-139,445,593,4000,4444,995-999,8998,2745,4751,1434
add action=drop chain=prerouting protocol=udp src-port=\
135-139,445,593,4000,4444,995-999,8998,2745,4751,1434
add action=drop chain=prerouting dst-address-list="Lista Negra" in-interface=\
bridge1 log=yes src-address-list=blocklistde_ftp_list
add action=drop chain=prerouting dst-address-list="Lista Negra" in-interface=\
bridge1 log=yes src-address-list=malwaredomainlist_list
add action=drop chain=prerouting dst-address-list="Lista Negra" in-interface=\
bridge1 log=yes src-address-list=ads_list
/ip firewall service-port
set ftp disabled=yes
set tftp disabled=yes
set irc disabled=yes
set h323 disabled=yes
set sip disabled=yes
set pptp disabled=yes
set udplite disabled=yes
set dccp disabled=yes
set sctp disabled=yes
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/ip ssh
set allow-none-crypto=yes forwarding-enabled=remote
/system clock
set time-zone-name=Europe/Madrid
/system leds
add disabled=yes leds="wlan1_signal1-led,wlan1_signal2-led,wlan1_signal3-led,w\
lan1_signal4-led,wlan1_signal5-led" type=wireless-signal-strength
add leds=wlan1_tx-led type=interface-transmit
add leds=wlan1_rx-led type=interface-receive
/system scheduler
add interval=4w2d name=reiniciar on-event="/system reboot" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=nov/04/2019 start-time=05:00:00
add interval=5m name=ddns on-event=no-ip policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=nov/14/2019 start-time=10:14:35
add interval=2d name="blaklist update" on-event=blaklist policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=nov/27/2019 start-time=22:18:58
/system script
add dont-require-permissions=no name=ddns owner=xx policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source="#\
add dont-require-permissions=no name=blaklist owner=xx policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source="/\
tool fetch url=\"https://blocklister.gefoo.org/blocklistde_ftp\" dst-path=\
\"ftp_list.rsc\"; import file-name=\"ftp_list.rsc\";\r\
\n\r\
\n/tool fetch url=\"https://blocklister.gefoo.org/ads\" dst-path=\"ads.rsc\
\";/import file-name=\"ads.rsc\";\r\
\n\r\
\n\r\
\n/tool fetch url=\"https://blocklister.gefoo.org/malwaredomainlist\" dst-\
path=\"malware_list.rsc\";/import file-name=\"malware_list.rsc\";\r\
\n"
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN